Carbanak – One of the most successful cybercriminal gangs ever that's known for the theft of one billion dollars from over 100 banks across 30 countries back in 2015 – is back with a BANG!
The Carbanak cyber gang has been found abusing various Google services to issue command and control (C&C) communications for monitoring and controlling the machines of unsuspecting malware victims.
Forcepoint Security Labs researchers said Tuesday that while investigating an active exploit sent in phishing messages as an RTF attachment, they discovered that the Carbanak group has been hiding in plain site by using Google services for command and control.
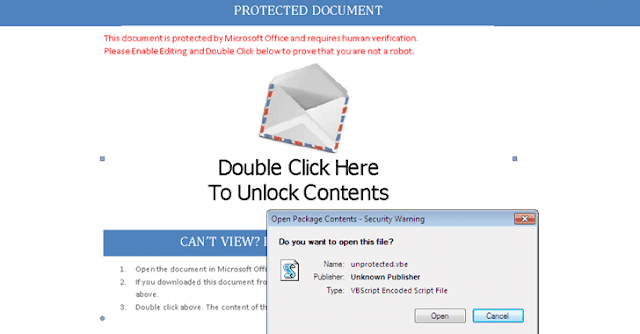
"The Carbanak actors continue to look for stealth techniques to evade detection," Forcepoint's senior security researcher Nicholas Griffin said in a blog post. "Using Google as an independent C&C channel is likely to be more successful than using newly created domains or domains with no reputation."The RTF document features an embedded OLE object that contains a VBScript (Visual Basic Script), which is previously associated with the Carbanak malware, and uses social engineering to trick victims into clicking on an envelope image to "unlock the contents."
It turns out that the envelope image actually hides the embedded OLE object, so as soon as the victim double-clicks that picture, a dialog box opens asking if the victim wants to run the file unprotected.vbe.
If the victim runs the file, Carbanak's VBScript malware will get executed, and, according to Forcepoint, the malware will "send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services."
If the victim runs the file, Carbanak's VBScript malware will get executed, and, according to Forcepoint, the malware will "send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services."
Besides VBScript malware, Forcepoint researchers also discovered a new 'ggldr' script module encoded inside the main VBScript file along with various other VBScript modules, capable of using Google services as a command and control channel.
"The ‘ggldr’ script will send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services," "For each infected user a unique Google Sheets spreadsheet is dynamically created to manage each victim," Griffin said.
"The use of a legitimate third party service like this one gives the attacker the ability to hide in plain sight. It is unlikely that these hosted Google services are blocked by default in an organization, so it is more likely that the attacker will establish a C&C channel successfully."
Forcepoint researchers reckon it is probable that the hacking group is using Google services because these services are allowed by default at many companies and organizations, which makes it easier for hackers to exfiltrate data and send instructions.
Carbanak, also known as Anunak, is one of the most successful cybercriminal operations in the world and is a highly organized group that continually evolves its tactics to carry out cyber crime while avoiding detection by potential targets and the authorities.
The group was first exposed in 2015 as financially-motivated cybercriminals targeting mainly financial institutions. Since it started operating in 2013, Carbanak has stolen upwards of $1 Billion from more than 100 banks across the globe.
Forcepoint has already notified Google of the issue, and its researchers are working with the web technology giant on this particular abuse of its legitimate web services.
Carbanak, also known as Anunak, is one of the most successful cybercriminal operations in the world and is a highly organized group that continually evolves its tactics to carry out cyber crime while avoiding detection by potential targets and the authorities.
The group was first exposed in 2015 as financially-motivated cybercriminals targeting mainly financial institutions. Since it started operating in 2013, Carbanak has stolen upwards of $1 Billion from more than 100 banks across the globe.
Forcepoint has already notified Google of the issue, and its researchers are working with the web technology giant on this particular abuse of its legitimate web services.





0 comments:
Post a Comment